What is 2-step verification and how it works

Before getting into What is 2-step verification lets discuss a few other points. Internet is a platform where nothing is 100% safe, i.e. your details bank account, password or anything can be hacked. There is nothing in the world of the internet that cannot be hacked by hackers. In that case, we should enhance our security, to make it more and more difficult for hacking attackers to bypass it. The feature of two-step verification is introduced to solve this security enhancement purpose. You must be using 2-step verification in many of the applications. So, today I will discuss – What is 2-step verification and how it works.
Nowadays, everyone is using “two-step verification” (2-step verification) to keep their account safe. This feature is used in every online application. For example: in accessing internet banking, social media accounts like Facebook, WhatsApp, etc., in your email and other accounts. It is also used while you pay for anything online with the credit card or debit cards etc. This security feature is used to protect your accounts from hacking and such attacks.
What is the 2-step verification process?
Two-step verification, which we also have known as Two Factor Authentication (2FA), is a security layer that makes your accounts more secure. That is, it enhances the security of your accounts to another level. We can also say that it doubles up the security checks of our accounts to protect them from attacks.
Mostly, people use the same password for all of their online accounts, whether it is a mailing account or a social media account or any other one. People do so because memorizing different passwords for different accounts is really difficult. But keeping the same password for all or multiple accounts gives ease to the hackers. If one of your accounts is hacked, then it will be easier for the hackers to hack all of your accounts.
Here, 2 Step Verification is very useful. If you have enabled two-step verification and if a hacker knows your password then that hacker cannot hack your account. As the hacker will have to go through the 2 step verification for that specific account, then only the attacker can access your account.
How 2-Step Verification works
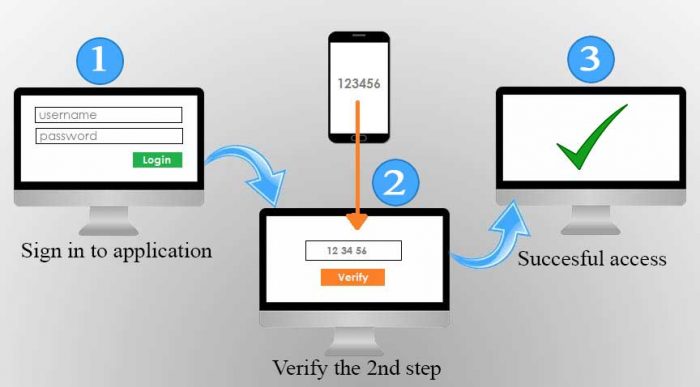
The perfect definition is: “2-Step Verification is a part of multi-factor authentication. This is a method to authenticate the user by using the combination of two identities which can be something the user knows or something the user has or something the user is.”
Now you must have the question that how two-step verification works and how it secures our accounts. So, I will tell you how 2-Step Verification works and how it prevents your account from being hacked and provides you double security.
You must have heard about OTP, that is One Time Password. This is a very common word if we are an online user. OTP is the commonest process of providing 2-step authentication. Some applications use this feature of OTP on a mandatory basis, like in online banking and other financial accounts. And some provide the option to choose it or not like in social media and email accounts.
How to use 2-step verification by OTP
While using two-step verification by OTP, you need to have a mobile phone with the registered mobile number. If you or anybody else try to login to your account with this feature enabled, with user name and password. Then an OTP will come on that number in the form of SMS. The person will have to enter that OTP to get access to that account. If the person is authentic and has the device, then only he can log in, otherwise not. In this way, this 2-step authentication process makes your account secure.
Other than OTP, there are also many different methods that can be by device popup, Authentication Key, Key in hardware form, etc. Among all, OTP is the easiest one for users.
Advantages and disadvantages of 2 Step Verification
Advantages of 2-Step Verification:
- It doubles up the security of your accounts
- Prevents your accounts from unauthorized access
- Makes online transaction safe which is very necessary
Disadvantages of 2-Step Verification:
The biggest and main disadvantage is if you do not have your mobile number or in case you have lost your phone, then you may have trouble logging in because the OTP that comes in 2 step verification is your mobile number. If you do not have your mobile number, then you will not be able to log in until you get it back, which is not that difficult. Some applications do also have other options to recover accounts in such situations.
How to enable two-step authentication
To enable this, go to your account settings and you will get an option in the security section with the name like 2 step Verification or two-factor authentication or multi-factor authentication or verification features. You can enter that section and follow the steps. By choosing the given options, you can enable or disable the security features of your account.
- How to enable 2-step verification in Gmail/ Google Account?
- What is Google Firebase? What services does it provide?
- How to change Phone Number in Gmail or Google account
Suggestions to protect your account
If you want to protect your account from being hacked, then you must enable a 2-step Verification for your account. The other tips to secure your accounts are below:
Use a strong password for your accounts which should contain alphanumeric values with special symbols. Like: HIsecuriy23#$
- You should never use your name or phone number in your passwords like name123, Name#2
- Also, do not use the same passwords in your multiple accounts.
- You should change your passwords regularly after some time or a few months.
- Never ever share your password with anyone.
- Also, prefer to use two-step verification in all of your accounts.
Today I explained to you about 2-Step Verification which you can use in your accounts to protect them. So, now you must be aware of the advantages of 2 Factor Authentication, its advantages and how to use this. Do let me know whether you found it useful or not in the comments below. If you still have any questions, do ask your questions in the comments and share them to keep others secure.







Leave a Reply