What is Pass-through Authentication?

When we configure Azure AD connect to create a Hybrid environment (On Premises + Azure), we get three authentication solutions. Pass-through Authentication is one of those Authentication solutions as described below.
Before we start let’s do a little recap on Azure AD and Azure AD Connect concepts.
What exactly is Azure AD?
As we have local Active Directory or Active Directory Directory Services (ADDS) in On Premises, in the same way Azure Active Directory is a directory service on Microsoft Cloud (Azure). Azure AD manages users, applications and other cloud objects. It also provides a highly secured environment when integrates with Azure ATP (Azure Advanced Threat Protection), Cloud App Security and solutions like Conditional Access Policy and much more. This attract On Premises organizations to migrate to Azure.
Now, what is Azure AD Connect?
Azure Active Directory Connect is a solution to synchronize your On Premises objects and attributes with Azure AD. Using Azure AD Connect, organizations can leverage their users to use both On Premises and Azure applications using their Active Directory credentials. This way, they don’t have to remember multiple passwords for different applications. Along-with that, they can enhance their experience using Single Sign On (SSO) and Seamless Single Sign On (SSSO).
Prerequisites to install Azure AD Connect:
It can only be installed on Windows Servers 2012 R2 or later. You should consider directory cleanup using “Idfix” tool.
Hybrid authentication solutions provided by Azure AD Connect:
- Password Hash Authentication
- Pass-through Authentication
- Federation
What happens when we configure Azure AD Connect with Pass-through Authentication:
Initialization of Pass-through Authentication:
As shown in the diagram above: The moment you select “Pass-through” option while configuring Azure AD Connect and enter Azure AD Global Admin credentials, it installs an agent- Pass-through Agent (PTA). Now, PTA generates public and private keys for AD users’ authentication. PTA keeps the private keys and shares the public keys with Azure AD.
Now, as we know that Azure AD has an in-built SQL DB, it puts those public keys in this SQL DB. Then AAD generates the certificate for future authentication and this certificate gets stored in the domain controller’s certificate store.
This creates a secure channel between AAD’s Service Bus Que (SBQ) and Pass-through Agent (On Prem). All the future transactions for authentication are done through this secure channel.
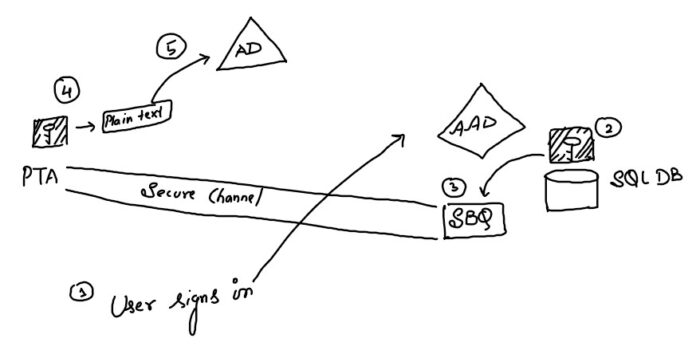
How PassThrough Agent (PTA) authenticated an AD user accessing Azure service:
As shown in the diagram above: When an end user enters his credentials to access any Azure service (e.g. SharePoint Online), the authentication request goes to Azure AD. Now, Azure AD encrypts the public key that it kept in its SQL DB and put it on its SBQ. Then SBQ contacts PTA which has the private key. PTA decrypts the password using its private key and then forwards the authentication request to On Prem AD, then AD authenticates the user.
Hope this article helped you understand PassThrough Authentication. Please feel free to write your queries in the comment box below. We highly encourage your queries as it helps us to improve our content.


Leave a Reply